My Journey to Firejail
Firejail is not new or trendy, so the full and detailed documentation is unsurprisingly easy to look for on the Internet. I just want to sum up about some specific use cases that one regular internet user would practice it daily.
Consent to private data granted
Firejail helps to control what resource of your machine to be exposed to the running apps.
Okay, but a picture is worth a thousand words.
Let’s look what a browser can access in your $HOME directory:
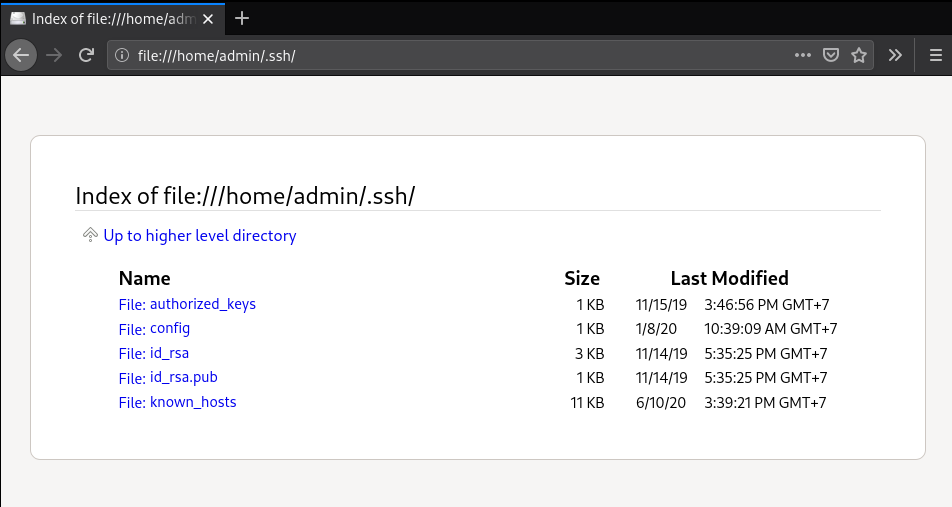
A well-behaving app would never touch that extreme sensitive information. But not every app behaves well (intentionally or not). And better be cautious than regret.
A jailed running app will only see what it’s supposed to be able to reach:
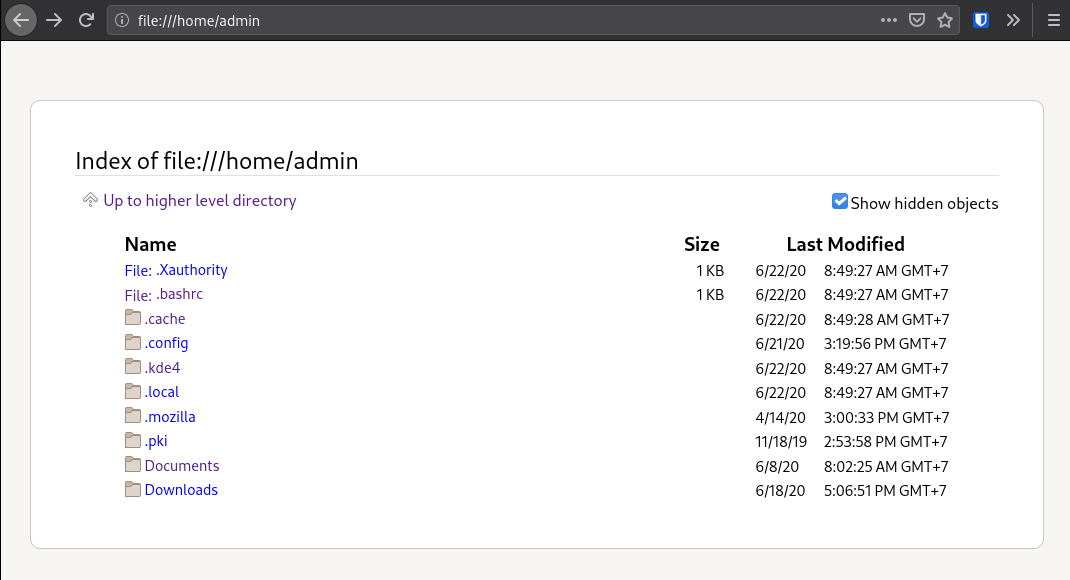
This is the default profile of almost the most popular browsers out there, so out-of-the-box, you’re good to go, no need for further configuration.
Memory limitation
Another feature that did improve my web surfing experience is the limitation of memory that my firefox instant can use. My corporation’s project management application (once in a while) suffers mem leak. The 8GB memory allocated prevents the whole system from freezing from time to time. This eventually prevents some badly implemented front-end apps to swallow our system memory. Of course, the free memory is sometimes the wasted memory, but a frozen machine is totally a bulk of the metal.
File: ~/.config/firejail/firefox-developer-edition.local
# Limit memory
rlimit-as 8000000000
Other resource limitations are available as well: CPU, number of files to write, size of files to write…
DBus whitelisted
The effectiveness of using firejail is crystal clear. However, the tradeoff between convenience and security is too obvious.
For computer users that English is not their mother tongue, input-method is one of the necessities installed in their workstation. A jailed running firefox is not able to communicate with dbus out-of-the-box. This results in a custom config:
File: ~/.config/firejail/firefox-developer-edition.local
ignore nodbus
Of course, that can only be effective if the profile is correctly imported.
$ firejail --audit firefox-developer-edition
Reading profile /etc/firejail/firefox-developer-edition.profile
Reading profile /home/admin/.config/firejail/firefox-developer-edition.local
Reading profile /etc/firejail/firefox.profile
Reading profile /etc/firejail/whitelist-usr-share-common.inc
Reading profile /etc/firejail/firefox-common.profile
Reading profile /etc/firejail/disable-common.inc
Reading profile /etc/firejail/disable-devel.inc
Reading profile /etc/firejail/disable-exec.inc
Reading profile /etc/firejail/disable-interpreters.inc
Reading profile /etc/firejail/disable-programs.inc
Reading profile /etc/firejail/whitelist-common.inc
Reading profile /etc/firejail/whitelist-var-common.inc
Parent pid 35179, child pid 35180
[...]
Play well with Yubikey
Another inconvenience, this time, affecting yubikey users, is that Firejail also affects the WebAuthn API by default. The services which use the told API are unable to communicate with the yubikey. The key was inserted but the LED didn’t flash when the service asked for it.
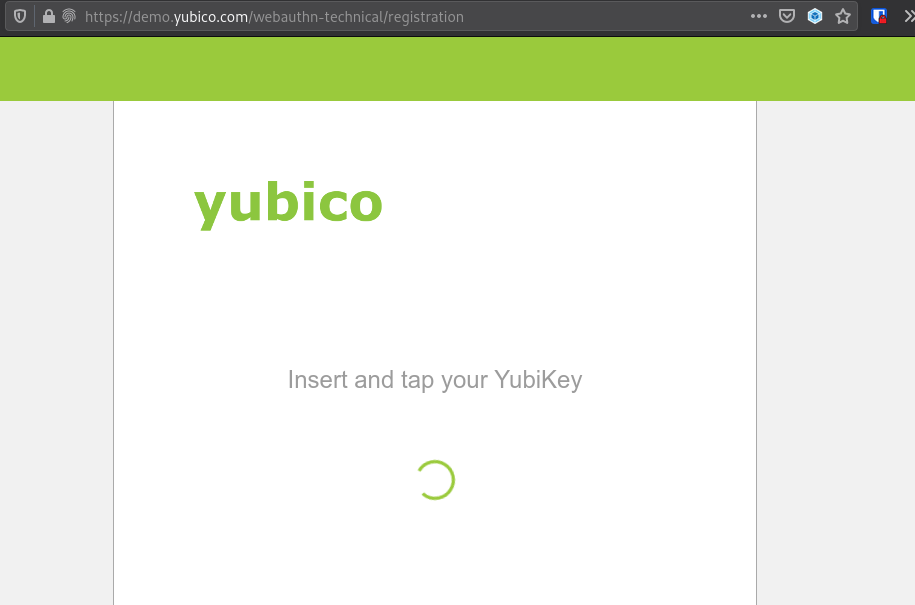
Let’s try a custom config:
File: ~/.config/firejail/firefox-developer-edition.local
ignore nou2f
Everything worked as expected.
Some other issues that I experience are the inability of opening a link to default browser, set Firefox as the default browser, mime type for the default apps… I, unfortunately, didn’t manage to solve it, even though a ton of research is done from time to time.
Pleased to hear from your sharing.